|
|
E-mail Info add-in for Outlook |
Phishing attempts can be a serious problem for individuals and businesses.
E-mail has never been the most secure medium around and with the ability to send mass e-mails in a short time, it makes an ideal means of exploitation.
With companies nowadays requesting personal e-mails and creating mailing lists, security breaches make it very easy for these lists to be used for malicious reasons.
In addition to this, unscrupulous companies sell these mailing lists themselves, making it possible to receive unwanted and dangerous e-mails from almost anywhere.
Filters from large e-mail providers have become more and more sophisticated and manage to catch most of the spam, phishing and virus e-mails,
but new, more insidious, phishing attempts keep coming and filters can't always keep up.
Sometimes a suspicious e-mail still manages to slip through.
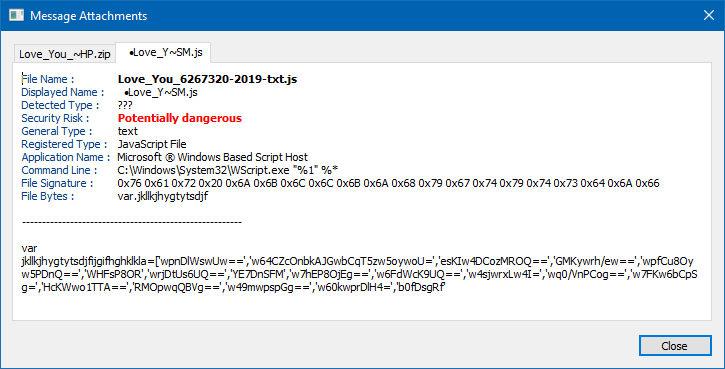
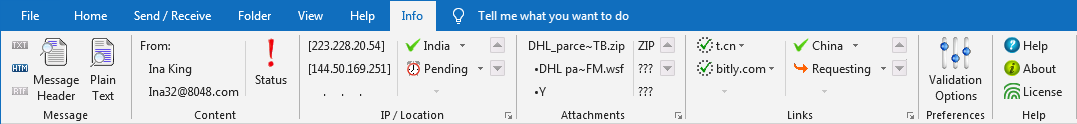
This add-in for Outlook provides an opportunity to learn a lot of information about an e-mail before opening it.
The add-in analyzes the location of the servers the e-mail passed through, the attachments that came with the e-mail
and also examines the links contained. A user, in case of a suspicious e-mail, can look at all this additional
information to decide to open or delete the e-mail, helping avoid a phishing scam or a virus infection.
|
Full Version
|
|---|
| Unlimited |
| E-mail IP Location |
| Multiple Geo IP Providers |
| Analyze Attachments |
| Inspect Links |
| Price: $5.99 |
|
License key will be e-mailed |
|
| Outlook | 32 bit | 64 bit |
|---|---|---|
| 2007 | ||
| 2010 | ||
| 2013 | ||
| 2016 | ||
| 2019 | ||
| 365 |
| Outlook | 32 bit | 64 bit |
|---|---|---|
| 2007 | ||
| 2010 | ||
| 2013 | ||
| 2016 | ||
| 2019 | ||
| 365 |
© 2019-2020 Rare Phoenix Soft, All Rights Reserved.